Hier stehen die veralteten Seiten - Teil 1
Der perfekte OpenSuse 13.1 Server ???
von Gert Redlich 4. Oktober 2014 - Auf www.howtoforge.com beschreibt der Author Falko Timme im März 2014, wie er einen aktuellen perfekten 64bit openSuse 13.1 Server "erzeugt".
www.howtoforge.com/the-perfect-server-opensuse-13.1-with-apache2-mysql-php-postfix-and-ispconfig-3
Darauf aufbauend soll es bei uns also eine Vorlage (zum Klonen) für eine universelle "virtuelle Maschine" mit allem Drum und dran werden. Das bedeutet, es geht hier nicht um das xen-Grundsystem, die xen-DOM 0, sondern um die Installation einer Vorlage für einen virtuellen xen-Gast, einer DOM U unter opensuse 13.1.
Nachdem ich erfahren musste, daß die 13.1 als DOM 0 Grundlage nicht funktioniert, bin ich für die xen-DOM 0 wieder zur Version 12.3 zurück gegangen - und die funktioniert. Also gehts es weiter mit der DOM U.
.
Falko Timme beschreibt (im März 2014) seine Ziele
I will use the following software:
.
- Web Server: Apache 2.4 with PHP 5
- Database Server: MySQL
- Mail Server: Postfix with virtual users
- DNS Server: BIND
- FTP Server: pureftpd
- POP3/IMAP: Dovecot
- Webalizer and AWStats for web site statistics
.
In the end you should have a system that works reliably and is easily manageable with the "ISPConfig 3" control panel.
Gesucht hatte ich nach "ISPConfig"
Ausschlaggebend war die Forderung, manche Server - wie den Mail-Server - einfacher verwalten zu können. Doch ISPConfig3 kann mehr, also testen wir das mal.
.
Meine Grundlagen sind jedoch professioneller Natur
Die Grundlage für diese Installation ist eben kein normaler PC oder ein Notebook, es sind mit XEN virtualisierte HP Profi-Server DL385-G5 in einem Data-Center weit ab von meinem Büro. Und der Zugang zu dem jeweiligen Server auf die DOM 0 geschieht über ssh-putty mit getunneltem VNC Viewer. Hilfsweise geht die Bedienung auch über die HP eigene iLO2 Server-Remote-Konsole, die immer funktioiniert. Die Installation der opensuse 12.3 als DOM 0 ist auf meinen Seiten hinreichend beschrieben worden.
Hier beginnt die Installation des XEN-Gastes.
Durch die DOM 0 ist die 64 Bit Version von opensuse bereits unabänderbar festgelegt und wird immer vorausgesetzt.
aus opensuse 12 mach opensuse 13
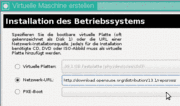
Die Installation von opensuse sei hier mal als bekannt vorausgesetzt. Da die DOM 0 mit Version 12.3 läuft, wird auch nur die letzte aktuelle Version von suse 12 vorgeschlagen. Das hindert uns aber nicht, dort die URL der Quelle auf 13.1 anzupassen (oder später auch auf 13.2 oder noch höher).
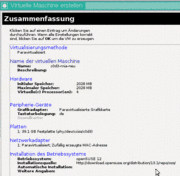
Der Gast bekommt mehr Speicher und 4 CPUs
In der initialen Maske des Installationsprogrammes des XEN VMM kann man den zu installierenden Gast konfigurieren und die Defaults überschreiben. Jeder Gast bekommt bei uns immer eine eigene Platte - nur für ihn ganz alleine.
Die minimale Server Selection
Wir bestimmen selbst, welche Module wir installieren und woher wir die nehmen wollen.
Wir sind draußen online im Internet und lassen auf jeden Fall die Firewall aktiviert !!!!
Der Autor dieser Vorschläge empfiehlt, die Firewall zu "de"-aktivieren. Ich empfehle genau das Gegenteil. Die Firewall muß immer aktiv bleiben und die jeweilgen Dienste werden explizit freigegeben. Die Ganoven vom Ende der Welt sind schneller, als Sie es sich vorstellen können.
Leider geht im VNC Client das drag and drop nicht,
darum brauchen wir neben dem immer noch über VNC laufenden DOM 0 "virtuellen machines manager" unbedingt den direkten ssh Consolen-Zugriff und den installieren wir noch mit der laufenden VNC Oberfläche. Wie das geht, muß hier auch vorausgesetzt werden. Dazu werden mit zypper die Programme htop, iftop, mc und .. (da war noch was) .. installiert.
Jetzt Zugang auf den neu erstellten Gast mit putty
Nach der Grundinstallation mit DHCP (da wird auch nicht geändert, denn es soll die Klone-Vorlage werden) verlassen wir die VNC Oberfläche und starten den Zugang auf Konsole mit der SSH Shell. Auf der VNC Oberfläche lasse ich später das Programm "htop" mitlaufen, um direkt zu sehen, was dieser Gast bzw. die jeweils angekurbelte Job tut.
Natürlich müssen jetzt alle Netwerkfunktionen über das virtuelle Interface ETH0 und die die xen bridge funktionieren, denn bis jetzt geschah alles über den sowieso funktionieren xen Manager im direkten Consolen Modus, bei dem noch keine funktionierenden Netzwerkadressen notwendig waren. Es sollte hier ein erster "reboot" ausgeführt werden, um zu testen, ob dieser Gast bis hierhin wieder problemlos startet und auch eine DHCP Adresse samt Gateway und Nameserver erhält.
.
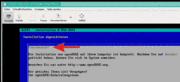
Die Minimalversion läft jetzt als Gast
Bei meiner opensuse 13.1 Minimalversion sind alle System-Updates bereits automatisch (per Default über autoYAST) durchgeführt worden. Und jetzt habe ich die große putty Text-Konsole für alle weiteren Arbeiten zur Verfügung.
.
Der Autor schlägt vor :
6 Install Some Basic Packages
zypper install findutils readline glibc-devel findutils-locate gcc flex lynx compat-readline4 db-devel wget gcc-c++ subversion make vim telnet cron iptables iputils man man-pages nano pico sudo perl-TimeDate
ich reduziere das auf
zypper install findutils readline findutils-locate gcc flex lynx compat-readline4 db-devel wget gcc-c++ subversion cron iptables iputils man man-pages nano pico sudo perl-TimeDate ---- und schon gar kein telnet
(also keine Compiler und devel Tools, kein telnet, vim, wir benutzen "joe" anstelle vi oder vim)
.
weiter geht es mit
7 Journaled Quota (wird aber übesprungen)
zypper install quota
Die Konfiguration überspringe ich vorerst, denn Platz ist genügend da.
.
weiter mit Vorschlag 8
8 Install Postfix, Dovecot, MySQL
zypper install postfix postfix-mysql mysql-community-server libmysqlclient-devel dovecot21 dovecot21-backend-mysql pwgen cron python
Und hier treten die ersten Probleme auf.
If you get the following message, please select to uninstall exim:
Problem: sendmail-8.14.5-85.1.2.x86_64 conflicts with postfix provided by postfix-2.9.6-1.2.1.x86_64
Solution 1: Following actions will be done:
do not install postfix-2.9.6-1.2.1.x86_64
do not install postfix-mysql-2.9.6-1.2.1.x86_64
Solution 2: deinstallation of sendmail-8.14.5-85.1.2.x86_64
Choose from above solutions by number or cancel [1/2/c] (c): <-- 2
und weiter :
mysql läuft nicht, auch nicht mit allen möglich Kniffs und Tricks.
Nach 2 Stunden googeln habe ich "zypper rm mysql" zum Löschen aufgerufen und mysql nocheinmal mit YAST nachinstalliert. Dann konnte ich mysql starten.
ln -s /usr/lib64/dovecot/modules /usr/lib/dovecot
jetzt kommt ein zweites reboot
jetzt joe /etc/my.cnf
und
change the line "sql_mode=NO_ENGINE_SUBSTITUTION,STRICT_TRANS_TABLES" to:
sql_mode=NO_ENGINE_SUBSTITUTION
systemctl enable mysql.service
systemctl start mysql.service
systemctl enable postfix.service
systemctl start postfix.service
systemctl enable dovecot.service
systemctl start dovecot.service
es dürfen keine Fehler auftauchen!!!
Wenn mysql nicht startet, fehlt eine Grundfunktionalität für später !!!
Warum das jetzt hier kommt, ist nicht schlüssig
Now I install the getmail package:
zypper install getmail
.
To secure the MySQL installation
# mysql_secure_installation
NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL MySQL
SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP CAREFULLY!
In order to log into MySQL to secure it, we'll need the current
password for the root user. If you've just installed MySQL, and
you haven't set the root password yet, the password will be blank,
so you should just press enter here.
Enter current password for root (enter for none): <-- ENTER
OK, successfully used password, moving on...
Setting the root password ensures that nobody can log into the MySQL
root user without the proper authorisation.
Set root password? [Y/n] <-- Y
New password: <-- yourrootsqlpassword
Re-enter new password: <-- yourrootsqlpassword
Password updated successfully!
Reloading privilege tables..
... Success!
By default, a MySQL installation has an anonymous user, allowing anyone
to log into MySQL without having to have a user account created for
them. This is intended only for testing, and to make the installation
go a bit smoother. You should remove them before moving into a
production environment.
Remove anonymous users? [Y/n] <-- Y
... Success!
Normally, root should only be allowed to connect from 'localhost'. This
ensures that someone cannot guess at the root password from the network.
Disallow root login remotely? [Y/n] <-- Y
... Success!
By default, MySQL comes with a database named 'test' that anyone can
access. This is also intended only for testing, and should be removed
before moving into a production environment.
Remove test database and access to it? [Y/n] <-- Y
- Dropping test database...
... Success!
- Removing privileges on test database...
... Success!
Reloading the privilege tables will ensure that all changes made so far
will take effect immediately.
Reload privilege tables now? [Y/n] <-- Y
... Success!
Cleaning up...
All done! If you've completed all of the above steps, your MySQL
installation should now be secure.
Thanks for using MySQL!
:~ #
Now your MySQL setup should be secured.
9 Amavisd-new, Spamassassin And Clamav
Install Amavisd-new, Spamassassin and Clamav antivirus
zypper install amavisd-new clamav clamav-db zoo unzip unrar bzip2 unarj perl-DBD-mysql
joe /etc/amavisd.conf
hier ändern :
[...]
$mydomain = 'ipw.net'; # a convenient default for other settings
$myhostname = "servervorlage1.$mydomain";
[...]
mkdir -p /var/run/clamav
ln -s /var/lib/clamav/clamd-socket /var/run/clamav/clamd
joe /etc/tmpfiles.d/clamav.conf
D /var/run/clamav 0755 root root -
joe /etc/init.d/amavis
[...]
start)
# ZMI 20100428 check for stale pid file
#if test -f $AMAVIS_PID ; then
# checkproc -p $AMAVIS_PID amavisd
# if test $? -ge 1 ; then
# # pid file is stale, remove it
# echo -n "(stale amavisd pid file $AMAVIS_PID found, removing. Did amavisd crash?)"
# rm -f $AMAVIS_PID
# fi
#fi
echo -n "Starting virus-scanner (amavisd-new): "
$AMAVISD_BIN start
#if ! checkproc amavisd; then
# rc_failed 7
#fi
rc_status -v
#if [ "$AMAVIS_SENDMAIL_MILTER" == "yes" ]; then
# rc_reset
# echo -n "Starting amavis-milter:"
# startproc -u vscan $AMAVIS_MILTER_BIN -p $AMAVIS_MILTER_SOCK > /dev/null 2>&1
# rc_status -v
#fi
;;
stop)
echo -n "Shutting down virus-scanner (amavisd-new): "
#if checkproc amavisd; then
# rc_reset
$AMAVISD_BIN stop
#else
# rc_reset
#fi
rc_status -v
#if [ "$AMAVIS_SENDMAIL_MILTER" == "yes" ]; then
# rc_reset
# echo -n "Shutting down amavis-milter: "
# killproc -TERM $AMAVIS_MILTER_BIN
# rc_status -v
#fi
;;
[...]
Because we have changed the init script, we must run
systemctl --system daemon-reload
now.
Ob ich das wirklich jetzt bereits aktivieren sollte, ist mit nicht klar.
To start clamav we need to download the database & proceed further with the command
freshclam
Note: It takes a lot of time to download the database, you are advised not to interrupt & do not stop the freshclam update service in between
To enable the services, run:
systemctl enable amavis.service
systemctl enable clamd.service
systemctl start amavis.service
systemctl start clamd.service
.
10 Install The Apache 2 Webserver With PHP5, Ruby, Python, WebDAV
Install Apache2 and suphp
zypper install apache2 apache2-mod_fcgid
Install PHP5:
zypper install php5-bcmath php5-bz2 php5-calendar php5-ctype php5-curl php5-dom php5-ftp php5-gd php5-gettext php5-gmp php5-iconv php5-imap php5-ldap php5-mbstring php5-mcrypt php5-mysql php5-odbc php5-openssl php5-pcntl php5-pgsql php5-posix php5-shmop php5-snmp php5-soap php5-sockets php5-sqlite php5-sysvsem php5-tokenizer php5-wddx php5-xmlrpc php5-xsl php5-zlib php5-exif php5-fastcgi php5-pear php5-sysvmsg php5-sysvshm ImageMagick curl apache2-mod_php5
Auch das klappt nicht richtig. Für einen Serveradmin ist die Kontrolle der diversen Runlevel samt dem Ein- und Ausschalten mittels YAST unverzichtbar.
zypper trägt offensichtlich die installierten Module nicht in die Liste von YAST-Runlevel ein. Das ist eine dicke Macke, mit der ich nicht (mehr) leben kann, schon gar nicht im Okt 2014. Diese primitiven Macken sollten wirklich alle bereits ausgemerzt sein.
und auf noch etwas muss man aufpassen
Die RPMs in den Repositories ändern sich.
Diese Befehlszeile geht so nicht mehr
zypper install download.opensuse.org/repositories/server:/php/openSUSE_13.1/x86_64/suphp-0.7.1-5.3.x86_64.rpm
hier muß man in
http://download.opensuse.org/repositories/server:/php/openSUSE_13.1/x86_64/
erst mal nachsehen, welches die aktuelle Version ist und die URL von Hand hinten dran hängen
wenn dann suphp installiert ist, gehts weiter :
Then run these commands to enable the Apache modules (including WebDAV):
a2enmod socache_shmcb
a2enmod suexec
a2enmod rewrite
a2enmod ssl
a2enmod actions
a2enmod suphp
a2enmod fcgid
a2enmod dav
a2enmod dav_fs
a2enmod dav_lock
a2enmod logio
chown root:www /usr/sbin/suexec2
chmod 4755 /usr/sbin/suexec2
a2enflag SSL
diese Methodik ist sinnvoller - also erst das Repository hinzufügen, dann erst installieren:
To add Python support, run:
zypper --gpg-auto-import-keys addrepo --name "Python Support (Apache_openSUSE_13.1)" download.opensuse.org/repositories/Apache:/Modules/openSUSE_13.1/ apache-Modules
zypper install apache2-mod_python
a2enmod python
Next we install phpMyAdmin:
zypper install phpMyAdmin
To make sure that we can access phpMyAdmin from all websites created through ISPConfig later on by using /phpmyadmin (e.g. www.example.com/phpmyadmin) and /phpMyAdmin (e.g. www.example.com/phpMyAdmin), open /etc/apache2/conf.d/phpMyAdmin.conf...
vi /etc/apache2/conf.d/phpMyAdmin.conf
... and add the following two aliases right at the beginning:
Alias /phpMyAdmin /srv/www/htdocs/phpMyAdmin
Alias /phpmyadmin /srv/www/htdocs/phpMyAdmin
[...]
Before starting apache we need to follow the link & make changes in httpd.conf
vi /etc/apache2/httpd.conf
Comment these lines & add these lines
#<Directory />
# Options None
# AllowOverride None
# Order deny,allow
# Deny from all
#</Directory>
<Directory />
Options None
AllowOverride None
Require all denied
</Directory>
Now start the Apache service
systemctl enable apache2.service
systemctl start apache2.service
Auch das schlägt beim esten Male fehl, der Apache startet nicht.
Also habe ich die obigen Aliase wieder rausgeschnmissen. Dann gehts.
.
10.1 PHP-FPM
Angeblich ist der "Fast Page Mode" seit einigen Jahren bereits in PHP fest verankert. Wieso brauchen wir den hier dennoch ??
Der Autor schlägt vor:
Starting with ISPConfig 3.0.5, there is an additional PHP mode that you can select for usage with Apache: PHP-FPM.
To use PHP-FPM with Apache, we need the mod_fastcgi Apache module (please don't mix this up with mod_fcgid - they are very similar, but you cannot use PHP-FPM with mod_fcgid). We can install PHP-FPM and mod_fastcgi as follows:
mod_fastcgi is available from a third-party repository which we can enable it as follows:
Next we install Fastcgi and PHP-FPM:
zypper install fastcgi php5-fpm
Now download and install mod_fastcgi:
cd /tmp
wget download.opensuse.org/repositories/home:/munix9/openSUSE_13.1/x86_64/apache2-mod_fastcgi-2.4.7_SNAP_0910052141-3.1.x86_64.rpm
rpm -i apache2-mod_fastcgi-2.4.7_SNAP_0910052141-3.1.x86_64.rpm
a2enmod mod_fastcgi
Before we start PHP-FPM, rename /etc/php5/fpm/php-fpm.conf.default to /etc/php5/fpm/php-fpm.conf:
mv /etc/php5/fpm/php-fpm.conf.default /etc/php5/fpm/php-fpm.conf
Change the permissions of PHP's session directory:
chmod 1733 /var/lib/php5
Then open /etc/php5/fpm/php-fpm.conf...
vi /etc/php5/fpm/php-fpm.conf
... and change error_log to /var/log/php-fpm.log:
[...]
error_log = /var/log/php-fpm.log
[...]
There's no php.ini file for PHP-FPM under OpenSUSE 13.1, therefore we copy the CLI php.ini:
cp /etc/php5/cli/php.ini /etc/php5/fpm/
Next open /etc/php5/fpm/php.ini...
vi /etc/php5/fpm/php.ini
... and set cgi.fix_pathinfo to 0:
[...]
; cgi.fix_pathinfo provides *real* PATH_INFO/PATH_TRANSLATED support for CGI. PHP's
; previous behaviour was to set PATH_TRANSLATED to SCRIPT_FILENAME, and to not grok
; what PATH_INFO is. For more information on PATH_INFO, see the cgi specs. Setting
; this to 1 will cause PHP CGI to fix its paths to conform to the spec. A setting
; of zero causes PHP to behave as before. Default is 1. You should fix your scripts
; to use SCRIPT_FILENAME rather than PATH_TRANSLATED.
; php.net/cgi.fix-pathinfo
cgi.fix_pathinfo=0
[...]
Next create the system startup links for php-fpm and start it:
systemctl enable php-fpm.service
systemctl start php-fpm.service
PHP-FPM is a daemon process that runs a FastCGI server on port 9000, as you can see in the output of
netstat -tapn
Next enable the following Apache modules...
a2enmod actions
a2enmod fastcgi
a2enmod alias
... and restart Apache:
systemctl restart apache2.service
.
11 Install PureFTPd
ob wir das später aktivieren, ist noch nicht raus.
Install the pure-ftpd FTP daemon. Run:
zypper install pure-ftpd
systemctl enable pure-ftpd.service
systemctl start pure-ftpd.service
Now we configure PureFTPd to allow FTP and TLS sessions. FTP is a very insecure protocol because all passwords and all data are transferred in clear text. By using TLS, the whole communication can be encrypted, thus making FTP much more secure.
OpenSSL is needed by TLS; to install OpenSSL, we simply run:
zypper install openssl
Open /etc/pure-ftpd/pure-ftpd.conf...
joe /etc/pure-ftpd/pure-ftpd.conf
If you want to allow FTP and TLS sessions, set TLS to 1 (wir wollen beides haben):
TLS 1
In order to use TLS, we must create an SSL certificate. I create it in /etc/ssl/private/, therefore I create that directory first:
mkdir -p /etc/ssl/private/
Afterwards, we can generate the SSL certificate as follows:
openssl req -x509 -nodes -days 7300 -newkey rsa:2048 -keyout /etc/ssl/private/pure-ftpd.pem -out /etc/ssl/private/pure-ftpd.pem
Country Name (2 letter code) [AU]: <-- Enter your Country Name (e.g., "DE").
State or Province Name (full name) [Some-State]: <-- Enter your State or Province Name.
Locality Name (eg, city) []: <-- Enter your City.
Organization Name (eg, company) [Internet Widgits Pty Ltd]: <-- Enter your Organization Name (e.g., the name of your company).
Organizational Unit Name (eg, section) []: <-- Enter your Organizational Unit Name (e.g. "IT Department").
Common Name (eg, YOUR name) []: <-- Enter the Fully Qualified Domain Name of the system (e.g. "server1.example.com").
Email Address []: <-- Enter your Email Address.
Change the permissions of the SSL certificate:
chmod 600 /etc/ssl/private/pure-ftpd.pem
Finally restart PureFTPd:
systemctl restart pure-ftpd.service
That's it. You can now try to connect using your FTP client; however, you should configure your FTP client to use TLS - see the next chapter how to do this with FileZilla.
.
12 Install den BIND nameserver
The BIND nameserver can be installed as follows:
zypper install bind
Create the BIND system startup links and start it:
systemctl enable named.service
systemctl start named.service
13 Install Webalizer And AWStats
Since ISPConfig 3 lets you choose if you want to use Webalizer or AWStats to create your web site statistics, we install both:
zypper install webalizer perl-Date-Manip
und wo ist awstats ??? geblieben ? - also von Hand nachinstallieren
.
in yast das repository anlegen
download.opensuse.org/repositories/network:/utilities/openSUSE_13.1
und dann awstats 7.1 nachinstallieren.
.
14 Install fail2ban und Jailkit und ntp undrkhunter
fail2ban can be installed as follows:
zypper install fail2ban
15 Install Jailkit
Jailkit can be installed like this:
zypper install download.opensuse.org/repositories/security/openSUSE_13.1/x86_64/jailkit-2.13-1.4.x86_64.rpm
16 Synchronize The System Clock
If you want to have the system clock synchronized with an NTP server do the following:
zypper install xntp
Then add system startup links for ntp and start ntp:
systemctl enable ntp.service
systemctl start ntp.service
17 Install rkhunter
rkhunter can be installed as follows:
zypper install rkhunter
18 Install SquirrelMail
To install the SquirrelMail webmail client, run:
zypper install squirrelmail-beta
Next we create the aliases /webmail and /squirrelmail right at the beginning of /etc/apache2/conf.d/squirrelmail.conf so that SquirrelMail can be accessed from any vhost (e.g. www.example.com/webmail or www.example.com/squirrelmail):
joe /etc/apache2/conf.d/squirrelmail.conf
Alias /squirrelmail /srv/www/htdocs/squirrelmail
Alias /webmail /srv/www/htdocs/squirrelmail
[...]
Next we create the directory /srv/www/htdocs/squirrelmail/data and give it sufficient permissions so that the www group can write to it:
mkdir /srv/www/htdocs/squirrelmail/data
chown root:www /srv/www/htdocs/squirrelmail/data
chmod 770 /srv/www/htdocs/squirrelmail/data
Again comment out this line
joe /etc/apache2/conf.d/mod_suphp.conf
[...]
DirectoryIndex index.php5
<Location />
# suPHP_AddHandler application/x-httpd-php
[...]
Then restart Apache:
systemctl restart apache2.service
Then configure SquirrelMail:
/srv/www/htdocs/squirrelmail/config/conf.pl
We must tell SquirrelMail that we are using Dovecot:
WARNING:
The file "config/config.php" was found, but it is for
an older version of SquirrelMail. It is possible to still
read the defaults from this file but be warned that many
preferences change between versions. It is recommended that
you start with a clean config.php for each upgrade that you
do. To do this, just move config/config.php out of the way.
Continue loading with the old config.php [y/N]? <-- y
Do you want me to stop warning you [y/N]? <-- y
SquirrelMail Configuration : Read: config.php (1.5.0)
---------------------------------------------------------
Main Menu --
1. Organization Preferences
2. Server Settings
3. Folder Defaults
4. General Options
5. User Interface
6. Address Books
7. Message of the Day (MOTD)
8. Plugins
9. Database
10. Language settings
11. Tweaks
D. Set pre-defined settings for specific IMAP servers
C Turn color on
S Save data
Q Quit
Command >> <-- D
SquirrelMail Configuration : Read: config.php
---------------------------------------------------------
While we have been building SquirrelMail, we have discovered some
preferences that work better with some servers that don't work so
well with others. If you select your IMAP server, this option will
set some pre-defined settings for that server.
Please note that you will still need to go through and make sure
everything is correct. This does not change everything. There are
only a few settings that this will change.
Please select your IMAP server:
bincimap = Binc IMAP server
courier = Courier IMAP server
cyrus = Cyrus IMAP server
dovecot = Dovecot Secure IMAP server
exchange = Microsoft Exchange IMAP server
hmailserver = hMailServer
macosx = Mac OS X Mailserver
mercury32 = Mercury/32
uw = University of Washington's IMAP server
gmail = IMAP access to Google mail (Gmail) accounts
quit = Do not change anything
Command >> <-- dovecot
SquirrelMail Configuration : Read: config.php
---------------------------------------------------------
While we have been building SquirrelMail, we have discovered some
preferences that work better with some servers that don't work so
well with others. If you select your IMAP server, this option will
set some pre-defined settings for that server.
Please note that you will still need to go through and make sure
everything is correct. This does not change everything. There are
only a few settings that this will change.
Please select your IMAP server:
bincimap = Binc IMAP server
courier = Courier IMAP server
cyrus = Cyrus IMAP serverhttp://download.opensuse.org/repositories/network:/utilities/openSUSE_13.1/noarch/
dovecot = Dovecot Secure IMAP server
exchange = Microsoft Exchange IMAP server
hmailserver = hMailServer
macosx = Mac OS X Mailserver
mercury32 = Mercury/32
uw = University of Washington's IMAP server
gmail = IMAP access to Google mail (Gmail) accounts
quit = Do not change anything
Command >> dovecot
imap_server_type = dovecot
default_folder_prefix = <none>
trash_folder = Trash
sent_folder = Sent
draft_folder = Drafts
show_prefix_option = false
default_sub_of_inbox = false
show_contain_subfolders_option = false
optional_delimiter = detect
delete_folder = false
force_username_lowercase = true
Press enter to continue... <-- ENTER
SquirrelMail Configuration : Read: config.php (1.5.0)
---------------------------------------------------------
Main Menu --
1. Organization Preferences
2. Server Settings
3. Folder Defaults
4. General Options
5. User Interface
6. Address Books
7. Message of the Day (MOTD)
8. Plugins
9. Database
10. Language settings
11. Tweaks
D. Set pre-defined settings for specific IMAP servers
C Turn color on
S Save data
Q Quit
Command >> <-- S
download.opensuse.org/repositories/network:/utilities/openSUSE_13.1/noarch/
SquirrelMail Configuration : Read: config.php (1.5.0)
---------------------------------------------------------
Main Menu --
1. Organization Preferences
2. Server Settings
3. Folder Defaults
4. General Options
5. User Interface
6. Address Books
7. Message of the Day (MOTD)
8. Plugins
9. Database
10. Language settings
11. Tweaks
D. Set pre-defined settings for specific IMAP servers
C Turn color on
S Save data
Q Quit
Command >> S
Data saved in config.php
Done activating plugins; registration data saved in plugin_hooks.php
Press enter to continue... <-- ENTER
SquirrelMail Configuration : Read: config.php (1.5.0)a2enmod socache_shmcb
---------------------------------------------------------
Main Menu --
1. Organization Preferences
2. Server Settings
3. Folder Defaults
4. General Options
5. User Interface
6. Address Books
7. Message of the Day (MOTD)
8. Plugins
9. Database
10. Language settings
11. Tweaks
D. Set pre-defined settings for specific IMAP servers
C Turn color on
S Save data
Q Quit
Command >> <-- Q
After you have created a website in ISPConfig, you can access SquirrelMail using the /webmail or /squirrelmail aliases:
19 ISPConfig 3
Das Programm "ISPConfig 3" war der Auslöser für diese ganze Operation hier
Before we install ISPConfig 3, make sure that the /var/vmail/ directory exists:
mkdir /var/vmail/
Download the current ISPConfig 3 version and install it. The ISPConfig installer will configure all services like Postfix, Dovecot, etc. for you.
You now also have the possibility to let the installer create an SSL vhost for the ISPConfig control panel, so that ISPConfig can be accessed using https:// instead of . To achieve this, just press ENTER when you see this question: Do you want a secure (SSL) connection to the ISPConfig web interface (y,n) [y]:.
cd /tmp
wget www.ispconfig.org/downloads/ISPConfig-3-stable.tar.gz
tar xvfz ISPConfig-3-stable.tar.gz
cd ispconfig3_install/install/
Now start the installation process by executing: php -q install.php
.
Die ISPConfig 3 Installation :
--------------------------------------------------------------------------------
_____ ___________ _____ __ _ ____
|_ _/ ___| ___ \ / __ \ / _(_) /__ \
| | \ `--.| |_/ / | / \/ ___ _ __ | |_ _ __ _ _/ /
| | `--. \ __/ | | / _ \| '_ \| _| |/ _` | |_ |
_| |_/\__/ / | | \__/\ (_) | | | | | | | (_| | ___\ \
\___/\____/\_| \____/\___/|_| |_|_| |_|\__, | \____/
__/ |
|___/
--------------------------------------------------------------------------------
>> Initial configuration
Operating System: openSUSE or compatible, unknown version.
Following will be a few questions for primary configuration so be careful.
Default values are in [brackets] and can be accepted with <ENTER>.
Tap in "quit" (without the quotes) to stop the installer.
Select language (en,de) [en]: <-- ENTER
Installation mode (standard,expert) [standard]: <-- ENTER
Full qualified hostname (FQDN) of the server, eg server1.domain.tld [server1.example.com]: <-- ENTER
MySQL server hostname [localhost]: <-- ENTER
MySQL root username [root]: <-- ENTER
MySQL root password []: <-- yourrootsqlpassword
MySQL database to create [dbispconfig]: <-- ENTER
MySQL charset [utf8]: <-- ENTER
Generating a 2048 bit RSA private key
.......................................................+++
.................................................+++
writing new private key to 'smtpd.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]: <-- ENTER
State or Province Name (full name) [Some-State]: <-- ENTER
Locality Name (eg, city) []: <-- ENTER
Organization Name (eg, company) [Internet Widgits Pty Ltd]: <-- ENTER
Organizational Unit Name (eg, section) []: <-- ENTER
Common Name (eg, YOUR name) []: <-- ENTER
Email Address []: <-- ENTER
Configuring Jailkit
Configuring Dovecot
Configuring Spamassassin
Configuring Amavisd
Configuring Getmail
Configuring Pureftpd
Configuring BIND
Configuring Apache
Configuring Vlogger
Configuring Apps vhost
Configuring Bastille Firewall
Configuring Fail2ban
Installing ISPConfig
ISPConfig Port [8080]: <-- ENTER
Do you want a secure (SSL) connection to the ISPConfig web interface (y,n) [y]: <-- ENTER
Generating RSA private key, 4096 bit long modulus
........++
.....................................++
e is 65537 (0x10001)
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]: <-- ENTER
State or Province Name (full name) [Some-State]: <-- ENTER
Locality Name (eg, city) []: <-- ENTER
Organization Name (eg, company) [Internet Widgits Pty Ltd]: <-- ENTER
Organizational Unit Name (eg, section) []: <-- ENTER
Common Name (eg, YOUR name) []: <-- ENTER
Email Address []: <-- ENTER
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []: <-- ENTER
An optional company name []: <-- ENTER
writing RSA key
Configuring DBServer
Installing ISPConfig crontab
no crontab for root
no crontab for getmail
Restarting services ...
redirecting to systemctl
redirecting to systemctl
redirecting to systemctl
redirecting to systemctl
redirecting to systemctl
redirecting to systemctl
redirecting to systemctl
redirecting to systemctl
Installation completed.
server1:/tmp/ispconfig3_install/install #
weiter mit ... lieber nicht ..
Clean up the /tmp directory: - NEIN, mache es nicht. Lasse es leben.
cd /tmp
rm -rf /tmp/ispconfig3_install
rm -f /tmp/ISPConfig-3-stable.tar.gz
--------------------------------------------------------------------------
Open /etc/suphp.conf...
vi /etc/suphp.conf
... and make sure that it contains
x-httpd-suphp="php:/srv/www/cgi-bin/php"
anstelle von
x-httpd-suphp="php:/srv/www/cgi-bin/php5"
towards the end of the file: (nur die 5 am Ende muss weg!!)
[...]
[handlers]
;Handler for php-scripts
x-httpd-suphp="php:/srv/www/cgi-bin/php"
[...]
--------------------------------------------------------------------------
Der ganze obige Kram ist überflüssig, das wurde über links bereits repariert.
in /srv/www/cgi-bin $ finden wir :
php -> /usr/bin/php-cgi
php5 -> /srv/www/cgi-bin/php
.
Afterwards you can access ISPConfig 3 under
http(s)://server1.example.com:8080/
or
http(s)://192.168.0.100:8080/
(http or https depends on what you chose during installation).
Log in with the username admin and the password admin (you should change the default password after your first login):
Nach dieser Installation : es funktioniert nicht
Irgend etwas ist schief gelaufen, das mit den zypper Installationen hat nicht geklappt, warum auch immer.
Da ist ein Neuanfang gefragt, aber mit yast und nicht mit zypper. Ich muss die Dienste alle in /etc/init.d überwachen können. Zum Beipiel zeigt
/etc/init.d/apache2 status an, daß der Apache unused sei, aber er läuft. Das ist Murks.
.
Zusatzinformationen und Links
19.1 ISPConfig 3 Manual
In order to learn how to use ISPConfig 3, I strongly recommend to download the ISPConfig 3 Manual.
On about 300 pages, it covers the concept behind ISPConfig (admin, resellers, clients), explains how to install and update ISPConfig 3, includes a reference for all forms and form fields in ISPConfig together with examples of valid inputs, and provides tutorials for the most common tasks in ISPConfig 3. It also lines out how to make your server more secure and comes with a troubleshooting section at the end.
19.2 ISPConfig Monitor App For Android
With the ISPConfig Monitor App, you can check your server status and find out if all services are running as expected. You can check TCP and UDP ports and ping your servers. In addition to that you can use this app to request details from servers that have ISPConfig installed (please note that the minimum installed ISPConfig 3 version with support for the ISPConfig Monitor App is 3.0.3.3!); these details include everything you know from the Monitor module in the ISPConfig Control Panel (e.g. services, mail and system logs, mail queue, CPU and memory info, disk usage, quota, OS details, RKHunter log, etc.), and of course, as ISPConfig is multiserver-capable, you can check all servers that are controlled from your ISPConfig master server.
For download and usage instructions, please visit www.ispconfig.org/ispconfig-3/ispconfig-monitor-app-for-android/.
.